Stop cybercriminals from getting a foot in the door
With so much business data and key services held in "the cloud", ensuring adequate protection is important for business continuity. Standard cloud services provide some basic defences but aren't always powerful enough on their own; strong cybersecurity involves layers of specialist protections to block or slow-down complex attacks.
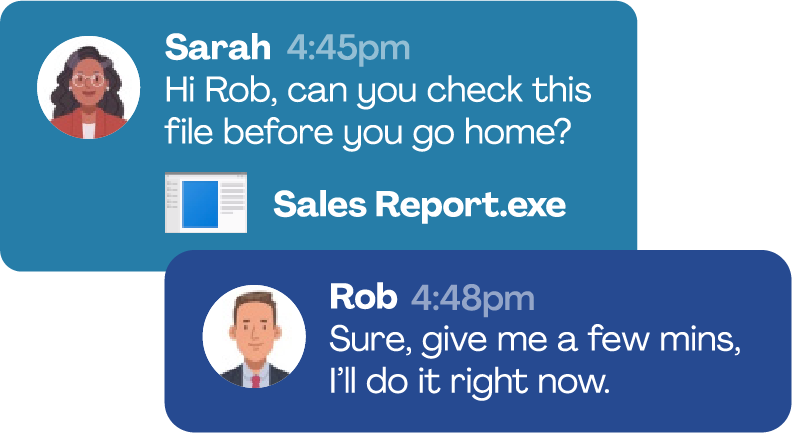
Phishing is a cyberattack in which scammers impersonate trusted entities to steal sensitive information such as passwords or financial details.
Phishing attacks come in many forms, but most rely on fake emails, messages, or websites that appear legitimate to deceive victims into clicking malicious links or providing confidential data.
A staggering 95% of cybersecurity breaches stem from human error, highlighting the critical need for awareness and vigilance in preventing such threats.
As ransomware attacks continue to surge in frequency and sophistication, many businesses are finding that the mail protection tools provided by their email platforms are no longer sufficient.
These basic defences often struggle to keep pace with the evolving tactics used by cybercriminals, who are increasingly adept at crafting phishing emails designed to bypass standard filters. This has led to a significant increase in successful ransomware infections, leaving companies vulnerable to devastating disruptions.
To effectively combat these threats, businesses need dedicated cybersecurity-focused specialists providing tools which offer advanced detection capabilities and robust protection against the rapidly growing menace of cloud-attacks.
Ongoing user-education through banners
Colour coded banners added to each and every email to help educate users over the longer term to dangers, anomalies and 'red flags'


Click protection
Scan the destinations of hyperlinks in real-time when clicked, blocking suspicious or malicious websites
Social graphing
Builds a profile of genuine interactions to better detect anomalies and impersonation attempts
Greymail identification
Quieten opt-in marketing emails where the frequency is impacting productivity and concentration
Data loss prevention
Catch sensitive information before it leaves your business
Deep file scans
Protecting against threats by looking at the behaviour of software components rather than their signatures
Messaging platforms
Collaboration systems like Teams and Slack are often implicitly trusted, but this makes them ideal arenas for attacks. Cloud based tools can inspect, block and flag messages and files shared on these platforms just like for internal e-mails.

Cloud storage
Protect file sharing services like Dropbox, Google Drive, & OneDrive from malware, ransomware and accidental or malicious data loss
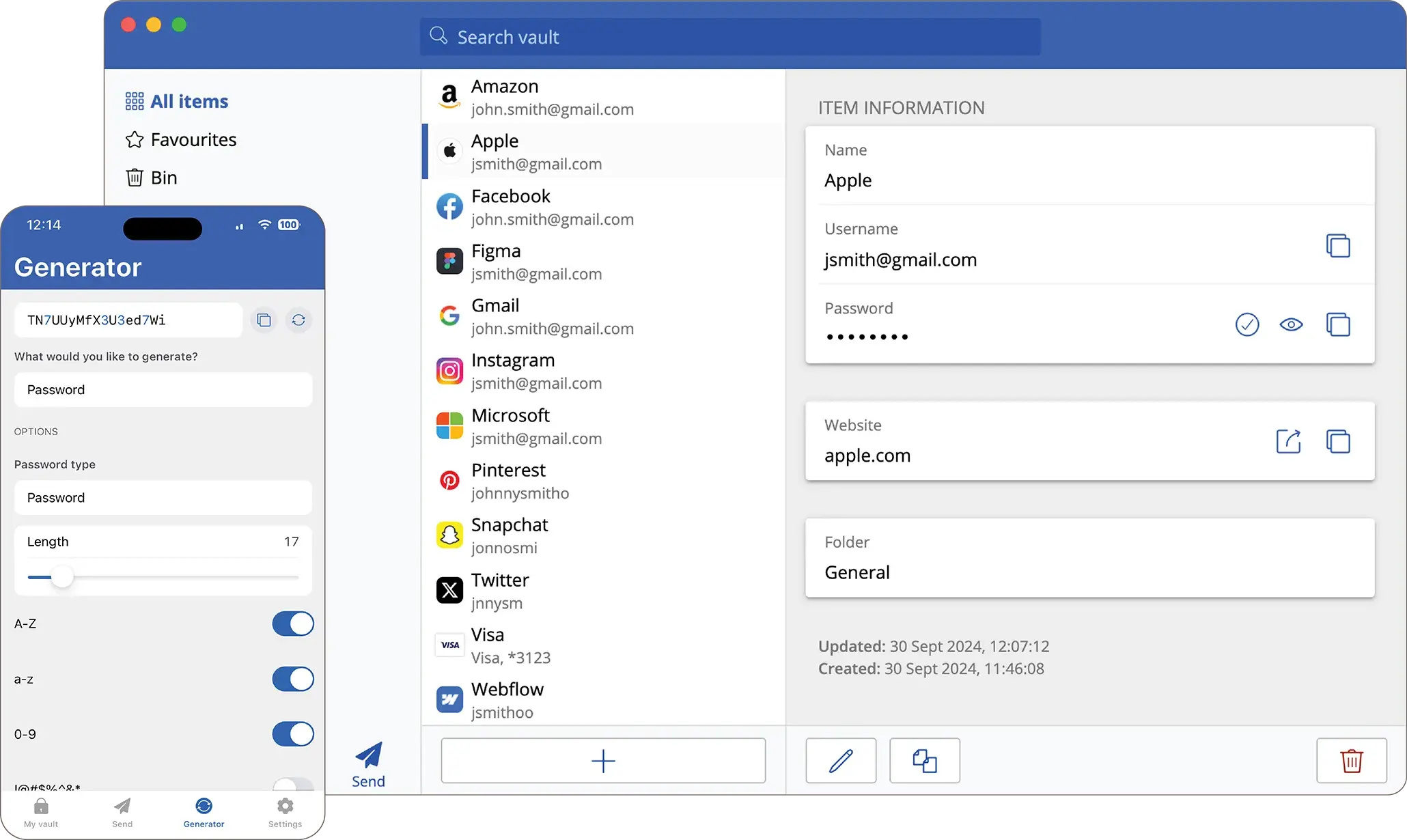
Securing your email and cloud accounts is just the first step in protecting your sensitive information. However, even the most robust security tools can be compromised without strong, unique passwords. That's why integrating a reliable password manager is essential—ensuring that all your accounts, across email and cloud services, remain secure and easily accessible only to you.
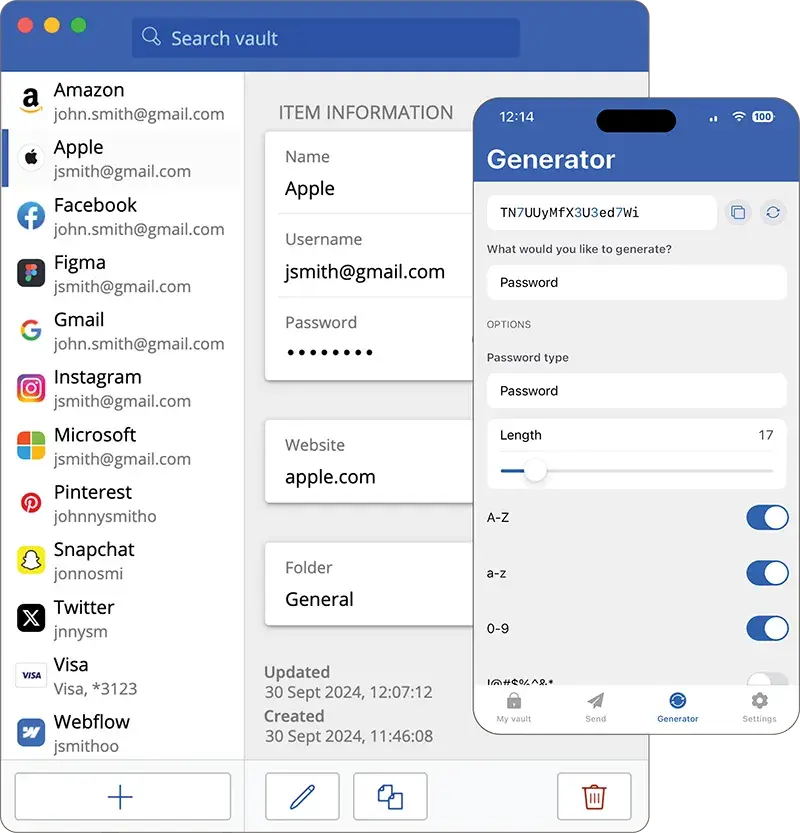
A password manager securely stores and encrypts your passwords, allowing you to create strong unique passwords for every account without having to remember them all
Over 70% of successful cyberattacks are the result of credential theft. However, having a complex long and unique password dramatically reduces the risk of you being impacted by this.
Our password manager solution is widely regarded as one of the best in the industry, and comes packed with tons of features, including several powerful options for businesses to ensure compliance and to aid with sharing between teams.
Password generator
Create secure credentials incapable of being cracked through brute force
Passkey storage and access
Passwordless, secure, streamlined logins which also prevent phishing attacks
Open-source security
Source code transparency, ensuring expert peer review of methodologies
Zero-knowledge encryption
End-to-end security ensures maximum privacy and avoids exposing data
Multi-platform
Clients for Windows, Mac, Linux, iOS, Android, or common web browsers
Store other private information
Keep other secrets such as notes, PIN codes, card or account numbers
Secure send
Send self-destructing fully encrypted one-time-secrets links to anyone
Everything in Core features, plus:
User groups
Add users into groups (e.g. accounts, marketing) to better manage access
Sharing credentials
Easy sharing of selected credentials (e.g. social media logins) to certain user groups or departments
Event & audit logs
Detailed and timestamped records of over 50 types of log events, allowing easy retracing of data access
Security reports
Access reports such as stolen passwords, to quickly identify and correct potential weaknesses
SSO integration
Use a supported external identity provider to login and sync users and groups
Everything in Business edition, plus:
Policies & custom roles
Enforce security rules for all users, such as minimum password length and 2FA
Recover user accounts
In the event of a forgotten master password, you can recover user accounts whilst also retaining all data
Complementary family account
For every user to share with up to five friends or family members
Self-host option
Run the server application in your own hosted environment, for compliance or data sovereignty reasons, whilst also maintaining compatibility with all client applications


This service can be Managed By Enlink which brings the following benefits:
Planning & design
We carefully assess your technical and business requirements ensuring a service tailored to your needs, balancing performance, scalability, and cost-effectiveness
Procurement & installation
We take care of everything, from sourcing equipment to managing installations, delivering a stress-free deployment
Ongoing management & support
Enjoy peace of mind with our continuous management, proactive diagnostics, upgrades and patches, and 24x7 fault support
Time and resource savings
We take pride in being conscientious, saving you valuable time and avoiding the headaches and costs of downtime

Use our simple wizard to ensure a quick turnaround of your quote, typically within one business day. If you need additional help or guidance, request a callback.
We may be able to offer you enhanced discounts if multiple services interest you: