Protecting your business from every angle
Safeguard your business from evolving cyber threats with comprehensive device protection and proactive vulnerability management designed to keep your network secure and resilient
At Enlink, we provide comprehensive device security solutions designed to safeguard your business from modern cyber threats.
Our suite of offerings leverages industry-leading technologies to ensure your devices, data, and networks remain secure and compliant. Two key components of our device security services are Endpoint Protection and Vulnerability Management—working together to deliver multi-layered protection for your business
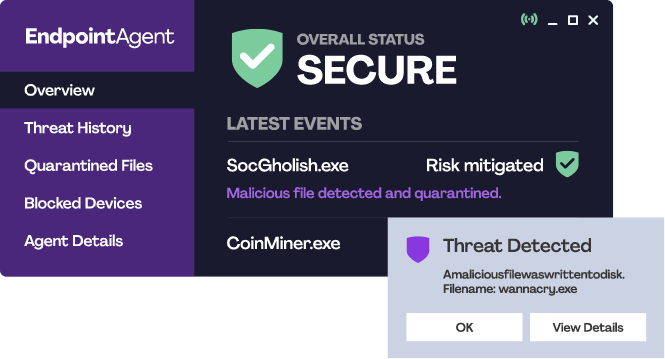
Cybercriminals can now bypass traditional antivirus scheduled scans and signature detection using more advanced tactics. Organisations need next-generation security solutions with AI, machine learning, and behavioural analysis to stay protected.
Using dedicated endpoint protection, especially as part of a managed service, provides that protection in four main stages:
The first line of defence for identifying the threat
Detect signatures
Using a comprehensive and up-to-date database
Heuristic analysis
Spots potential malicious patterns in the code
Behavioural analysis
Detecting software that behaves abnormally
Machine learning and AI
Identifying suspicious activities and anomalies
Stop malware before it does harm
Protect all endpoints
Installs on all major OS (Windows, Mac, Linux)
Respond intelligently
Quarantine infected systems from the network
Unmanaged devices
Identify and protect from new and guest devices
Speed of response
Automated actions from AI agents on the endpoint
Eliminate the threat and fix any damage
Assess the impact
Analyse the changes that were made to the system
Remote investigation
Expert manual diagnosis of the infected endpoints
Step-by-step rewind
Unpick the damage caused by the malware
One-click rollback
A single click to restore Windows systems
Understand the events to prevent reoccurence
Root cause forensics
Deep investigation into the method of attack
Strengthen defences
Apply patches and update necessary configurations
Locating weak points
Identifying vulnerabilities and human errors
Learning lessons
Prevent future incidents through staff training

Our vulnerability management service offers an easy-to-read risk assessment report with simple A-F grades.
This helps to measure and improve compliance with frameworks and regulations such as:


Our vulnerability management software allows you to scan your entire IT estate to search out and rectify weaknesses. These scans are categorised into Software, Network and Configuration checks.
Monitor applications and operating systems across the IT estate
Stay up-to-date
Keep OS, drivers and applications patched
Flag old systems
Easily spot end-of-life and unsupported systems
Enforce specific apps
Such as anti-virus, popup blockers, and team chat
Ban specific apps
Block installing games, streaming, p2p etc.
Track connected devices, anomalies and network weak spots
Asset inventory
List all network devices, services, and interfaces
Unknown devices
Discover threats hiding on your network
Network scanning
Open ports, file shares and exposed systems
Web server checks
SSL/TLS monitoring, exposed configurations
Discover weaknesses caused by misconfigurations
Users (Microsoft AD/Entra)
Check for active and inactive users, group memberships & rights policy objects and violations, failed login attempts and more
Devices
Check for local policies and firewall, system settings, network configuration, default passwords, expired licences and more
Supported systems include:




This service can be Managed By Enlink which brings the following benefits:
Planning & design
We carefully assess your technical and business requirements ensuring a service tailored to your needs, balancing performance, scalability, and cost-effectiveness
Procurement & installation
We take care of everything, from sourcing equipment to managing installations, delivering a stress-free deployment
Ongoing management & support
Enjoy peace of mind with our continuous management, proactive diagnostics, upgrades and patches, and 24x7 fault support
Time and resource savings
We take pride in being conscientious, saving you valuable time and avoiding the headaches and costs of downtime

Use our simple wizard to ensure a quick turnaround of your quote, typically within one business day. If you need additional help or guidance, request a callback.
We may be able to offer you enhanced discounts if multiple services interest you: